iESE is proud to announce the launch of the Cyber Centre of Excellence (CCOE) which is being showcased for the first time at the District Councils Network (DCN) annual conference in February. We believe the creation of the CCOE, which will represent a collaboration by UK public bodies underpinned by an Advisory Forum made up of some of the UK’s best brains in cyber security, will help drive forward major advances in the level of cyber protection in our local authorities and the UK public sector.
With our vision of making the UK the safest place to live, work and play online, the creation of the CCOE brings together the most knowledgeable and well-respected people in the industry to understand the cyber threats we face and how to address them. Through this expertise and member collaboration we aim to stay abreast and ahead of the growing and ever-present threat, offering peace of mind to the UK public sector.
We aim to make military grade support, products, training and advice available to the public sector by understanding what best-of-breed protection is and making this knowledge and these innovations available to procure simply at high street prices through our collective purchasing power. Essentially, the CCOE will offer a one-stop-shop to assist members throughout their cyber security journey from implementation and beyond. It does not aim to replace other organisations, such as the National Cyber Security Centre (NCSC), but aims to give practical guidance on implementing cyber security advice and standards and will also be well placed to assist if things go wrong.
To find out more about the CCOE, please go to www.ccoe.org.uk or contact us directly at [email protected]
Local Authorities Urged to get Involved with the CCOE
LOCAL AUTHORITIES AND OTHER PUBLIC BODIES ARE BEING URGED TO GET INVOLVED WITH THE NEWLY-FORMED CYBER CENTRE OF EXCELLENCE (CCOE) WHICH WAS SHOWCASED FOR THE FIRST TIME AT THE DISTRICT COUNCILS NETWORK (DCN) ANNUAL CONFERENCE IN FEBRUARY.
The CCOE will offer access to training, advice, products and services backed up by a group of advisers who will keep the CCOE abreast of cyber threat and up to date with new innovations. Any products and services offered under the umbrella of the CCOE will be tried and tested for the public sector. The initiative aims to offer military-grade protection at high-street prices through utilising iESE’s connections and collective purchasing power.
“At the moment there is a perfect storm where the complexity and frequency of attacks on local government are increasing. The innovation in the attacker is huge but our response as a sector isn’t. We know that there are gaps in our defences, especially in terms of operational technology, and we are working on plugging those gaps before they become a major issue. We need to make this business as usual and not frightening. The CCOE will sit at the forefront of best practice and act as a one-stop-shop to ensure local authorities and other public bodies are as secure as possible in this ever-changing environment.”
Dr Andrew Larner, Chief Executive at iESE
Development of the CCOE has been led by an Advisory Forum of some of the most knowledgeable people in cyber security the country, including prominent legal experts, ex-military and ex-police personnel who have worked and continue to work in protecting the security of the country. “By synthesising and continually synthesising their knowledge and through member collaboration we will increase our ability to stay ahead of the game. If you want protection that is five years ahead in the opinion of those who protect the national security of the country, then get involved,” Dr Larner added.
Council Leader Shares Cyber Learning
IESE HOSTED A STAND AT THE RECENT ARAB INTERNATIONAL CYBERSECURITY EXHIBITION AND CONFERENCE IN BAHRAIN WHERE THE CENTRAL THEME WAS EMPOWERING GLOBAL COOPERATION IN CYBER SECURITY.
Councillor David Tutt, leader of Eastbourne Borough Council and Chairman of iESE attended alongside Dr Andrew Larner, Chief Executive at iESE. Cllr Tutt said there were some key messages he had taken away from the conference regarding local government. First was the need to raise awareness of the level of risk being faced and for the sector to stay regularly updated about new and emerging threats. Secondly, he said the conference highlighted that collaboration would be key in future on both a global and national level.
“What we need globally is to collaborate on the things that have gone wrong. Organisations tend to close ranks when something happens – we don’t want to say we’ve been attacked or that we paid a ransom or what the consequences were. We need to share that information if we want to protect each other. A key takeaway for me from the conference is that there is an enormous need for universal standards across the industry and adoption of those on a global basis,”
David Tutt
Cllr Tutt said a demonstration by an ethical hacker on a Tesla car showed how people with a little bit of know-how can cause issues for malicious purposes, fun or financial gain. “The UK local government has 10,000 cyberattacks a day. We have seen the impact on some local authorities, and it is not just the financial impact, although that is immense and runs into millions, it is the loss of data and personal information of residents getting out into a wider domain and the impact of not being able to run your services for your residents or not being able to run payroll for your staff,” he explained.
Cllr Tutt said the conference had further opened his eyes to the level of risk faced by UK public authorities. However, he added that he remained hopeful for the future due to the creation of the Cyber Centre of Excellence (CCOE) and its commitment to helping protect local authorities and the public sector from cyber risks.
Keeping your Organisation Secure
The Cyber Centre of Excellence (CCOE) is an initiative aimed at all local authorities and UK public bodies to help them stay abreast of cyber threats and give them access to easy-to-procure military-grade protection at high street prices through collective purchasing power. It will be able to assist with the full remit of what an organisation needs to do and know to stay as cyber secure as possible.
We know that navigating an ever-changing cyber security landscape is difficult for local authority leaders with many competing priorities and limited budgets. That is why the cyber security industry is coming together to create the CCOE – an initiative underpinned by an Advisory Forum of world class experts to help you navigate cyber security for your organisation.
The CCOE is a place for organisations to collaborate and share knowledge of threats. It will also act as a one-stop-shop to help those involved in cyber protection understand what their unique risks are and how to best tackle them.
Kurtis Toy CISSP, Managing Director of Onca Technologies, is a Virtual Chief Information Security Officer (vCISO) who has been appointed as the Convenor of the CCOE. He has been working alongside iESE to develop the Cyber Centre of Excellence (CCOE) and ensure the Advisory Forum represents the range of skills needed for a cyber and data secure organisation. Here, he outlines some of the current threats facing local authorities and terms commonly used in the cyber security landscape:
Phishing
‘Phishing’ describes an unwanted email that might contain dangerous content or have a hidden agenda. This could be in the form of a hyperlink or URL that redirects to a malicious site or downloads an attachment with hidden malicious content.
Multi Factor Authentication (MFA)
When logging in, we use at least one factor to identify ourselves, such as a password or PIN, through a smartphone or a secure USB key, or via a fingerprint or facial recognition. Multi-factor Authentication uses at least two of these methods to log in, helping prevent password compromise.
Zero Trust
‘Zero Trust’ is a term a used for both security models and network architectures. In both cases, the main concept is “never trust, always verify”. This means all devices, access or identities should not be trusted by default, even if they were previously trusted or are connecting through a known network or location. Zero Trust is often implemented to promote strong verification processes that are continually re- examined and re-established and provide minimum access privileges.
Zero Day
Although this sounds the same as Zero Trust, it is not directly related to Zero Trust security or architecture models. A ‘Zero Day’ vulnerability is a security flaw that has been discovered but there is no security patch for it yet. Once discovered, Zero Day flaws are often exploited very quickly so it becomes a race against time for the software provider to develop and distribute a security patch.
Layered Approach
A ‘Layered Approach’ is a term often used within information security. Whilst it sounds like this means one tier of security being layered on top of another, it really means multiple solutions should be put into effect to defend against the same or similar issues. The idea is to build a suite of defences to act as contingency plans for one another and should include security tactics for people, processes, and technology. The best approach is to have a failover for every avenue possible and review your security controls on an ongoing and regular basis.
Ransomware
Ransomware is a type of malware, malicious software, that blocks access to the victim’s data and threatens to keep it unavailable or even delete it unless the victim pays a ransom to the attacker. This is a very common type of attack so it’s highly important to take every possible precaution against them. Defences against ransomware include: adequate training for all staff, including scenario training; technological defences such as antimalware, email protections and even AI; ensuring backups are maintained and immutable (see below); updating software regularly to ensure patches for Zero Day vulnerabilities are in place and implementing robust access control policies.
Breach
A cyber security breach is an incident resulting in the unauthorised access of computer data, applications, networks, or devices which results in information being accessed without authorisation. A breach can cost a company a large amount of money, not just in shoring up defences to prevent further breaches but also for potentially stolen intellectual property or critical company data. If the breach also includes personal data, the ICO (Information Commissioner’s Office) must be informed within 72 hours of the organisation becoming aware of the breach. Fines may be issued under the GDPR if adequate protections for personal data were not in place.
Nation State Threats
Cyberattacks of this nature are initiated and sponsored by countries or geopolitical groups and are referred to as Nation State Threats, which aim to disrupt infrastructure, business, government and military. These types of attack can be particularly difficult to identify as the attackers often shift blame to cyber gangs, other foreign entities or hacktivist groups.
IoT and OT
IoT denotes the Internet of Things and includes technologies such as machine learning, machine-to- machine communications, big data, sensor data and other data collected on automated devices.
OT denotes Operational Technology and defines a specific category of hardware or software that functions to monitor and manage the performance and operation of physical devices. OT systems often support critical infrastructure and industrial operations.
Immutable Backups
An immutable backup is a copy of data that cannot be altered, deleted or changed in any way once the back-up has completed, not even by system administrators. This type of back up can be critical when a company needs to recover or restore data after it has been lost or damaged, whether through a cyberattack or a natural disaster.
Meet the CCOE Advisory Forum
The CCOE’s goal is to create an entirely new level of protection in the UK and help the public sector become resilient against cyber threats. A shared service in the best traditions for local public services ensures that we all have the best people, the best technology, and the best protection. Our team have unparalleled experience, having run the UK’s military cyber offence and defence capability, having built the defences of the Bank of England, and also hold clearance to work on national cyber defence infrastructure.
Sitting behind the CCOE is an Advisory Forum of some of the UK’s leading experts in cyber security. This group will keep the CCOE up to date with threats and abreast of new innovations. Here they share their biographies and their thoughts on the CCOE:
Kurtis Toy
Kurtis Toy is a Virtual Chief Information Security Officer (vCISO) who has been appointed as the Convenor of the CCOE. After gaining an MSc in Biology he worked for an oil servicing company where he ended up working in IT. He became responsible for the IT information security in the company, leading to him becoming Global IT coordinator. He then gained an MSc in Information Technology, next becoming Global IT Team Leader before leaving to establish his own company in 2016. Further qualifications he has gained since include becoming a GDPR Foundation and practitioner (Data Protection Officer), ISO 9001 internal auditor training and ISO 27001 lead implementor. He is also a CISSP (Certified Information Systems Security Professional). He describes the CCOE as giving local authorities access to an umbrella of protection akin to a “validated Google of cyber security knowledge”
Major General Martin Smith
Major General Martin Smith CB MBE is the Managing Director of CyberPrism, a cyber security company which protects Operational Technology (OT) and IT in the UK and internationally. Before joining CyberPrism, Major General Smith had a 33-year career in the Royal Marines, becoming Commandant General of the Royal Marines. He commanded the UK’s Amphibious Force and led the UK’s maritime counter terrorism force. He also founded the unit known as 30 Commando Information Exploitation Group. Major General Smith is pleased to be part of the CCOE Advisory Forum. “CyberPrism fills a gap in that there is very little knowledge and experience in operational technology in the marketplace. Playing our part in the CCOE helps fulfil the full range of services needed by local authorities to address their cyber vulnerabilities. The CCOE is an initiative in which no single company is pretending to be able to do everything. It is a joint force of a range of experts in their own fields which will work for the good of the public sector.”
Dane Clackworthy
Dane Clackworthy is Head of Business Development and Sales at CyberPrism, a cyber security company which protects Operational Technology (OT) and IT in the UK and internationally. Before joining CyberPrism, he had a 20-year career in the Royal Marines where he gained extensive experience in radio communications and information assurance. His positions included being Yeoman of Signals, the Chief Communication Manager for the UK’s Response Force Task Group. The RFTG was a Very High Readiness force of 1,500 personnel that could deploy worldwide in 5-days. More recently, he was the unit Data Protection Officer, IT Security Officer and was project lead for the aviation CIS infrastructure plan for the Queen Elizabeth-class aircraft carrier.
At CyberPrism, he continues to enjoy relaying technical information between stakeholders in plain language that everyone can understand. “My role in the CCOE will be to keep the forum up to date on best practice in securing OT in a clear concise way that brings real value. There is a general lack of awareness about OT risks. We look forward to helping local authorities and public service organisations take the necessary steps to understand and secure their vulnerabilities.”
Irene Coyle
Irene Coyle is Chief Operating Officer at OSP Cyber Academy, a managed service provider of cyber, information security, data protection training and education programmes. She joined OSP Cyber Academy after a 30-year career in the police force in a variety of roles, including that of Chief Inspector for recruitment within Police Scotland. During her career in the police force, Coyle held various roles which centred on protecting people’s data, including as Detective Inspector of the Public Protection Unit at Grampian Police. In this position she was Project Manager of the Grampian Police Vulnerable Persons Database, a project which was then rolled out across Scotland. Coyle is also a Data Protection Officer, a NCSC Certified trainer and holds a teaching degree. OSP Cyber Academy has joined with the CCOE to provide member access to its suite of training tools. “To be involved with the CCOE is great. This new group wants to provide the best that it can for local authorities which is admirable. It is not about driving high profit for the experts involved, it’s about driving the cyber resilience capability across communities. I am excited to see where it goes and being part of building cyber resilience across the public sector.”
Thomas McCarthy
Thomas McCarthy is the founder and Managing Director of OSP Cyber Academy. He has previously held various roles in training auditing and safety, including several positions in the energy sector. As someone with a wide range of industry contacts and knowledge, McCarthy has been instrumental in helping to establish the advisory forum for the CCOE. OSP Cyber Academy are a UK Government- certified managed service provider of cyber, information security, data protection training and education programmes. The company has joined with the CCOE to provide its members access to its suite of training tools.
“In the last five years I have been involved with just about every cyber organisation there is in the UK and overseas. The CCOE is one that has been designed and set up to make a difference and to deliver, as opposed to just talk about delivering. The problem with cyber is that it is an ever- evolving threat landscape and things change so rapidly that the only way you can stay resilient is by keeping up to speed with what is going on. I think the CCOE will do this and has the capability to deliver for all public sector bodies.”
Sandip Patel KC
Sandip Patel has been a Barrister for more than 30 years and was appointed Queen’s Counsel (QC), which is now known as King’s Counsel (KC), more than ten years ago. He became involved in cyber security law after being asked to prosecute several cases for the Crown Prosecution Service. His cases have included that of Glenn Mangham who stole Facebook’s source code from his bedroom in North England using an ordinary desktop computer and Seth Nolan-Mcdonagh, the boy who ‘almost broke the internet’. Patel is also Director of cyber security consultancy Quantum Resilience International and Chief Legal Advisor at OSP Cyber Academy. He is pleased to be involved with the CCOE to contribute knowledge of legal compliance and advise how this might evolve by looking to other countries. However, he warns that legal compliance is the minimum organisations should aim for. “Regulatory compliance is not cyber security in my view. We know the public sector is extremely vulnerable and I am pleased to play a part in helping protect these organisations.”
Niall Burns
Niall Burns is one of the founders and Chief Executive Officer at the specialist risk mitigation, business intelligence and loss prevention company Subrosa Group. He started his career in the Royal Marines and then subsequently within UK Special Forces Communications where it was instilled that sensitive information should be delivered in a direct and confidential manner. Subrosa has been helping keep people safe for more than 25 years, including advising clients on keeping data safe. Cyber Security services are now a large part of their remit. Its services include penetration testing of systems, networks, and web applications, identifying vulnerabilities in internal and cloud-based systems, and identifying configuration vulnerabilities. It can also help clients review and assess processes and policies. “Something like the CCOE where you have experts who are not confined by purchasing protocols will be invaluable to the public sector. It will be able to look at the pros and cons and it won’t be handcuffed to say you have to do this, this and this. Use us as the experts to check you are getting fit-for-purpose and quality products because a lot of people are mis-selling out there.”
Colin Jupe
Colin Jupe is CEO of Assurity Systems, a company which provides advanced cyber security solutions to a variety of sectors including local government. He is also a qualified General Data Protection (GDPR) practitioner and the Managing Director of VXPartners, a company which helps organisations become and remain compliant with UK Data Protection law. Prior to launching Assurity Systems, Jupe held a management consulting role where he predominantly assisted technology companies with marketing and finance strategy and was also formerly Director of a marketing database and data processing company. “UK government and PLC are under attack more than ever and those in charge of local government have enormous pressures extending from budgetary and personnel issues through to IT. Rich private organisations are poaching all the good cyber-IT professionals which means the public sector must outsource to get access to skills. The cyber protection industry is a vendor-led industry. Who can you trust? How do you know which is the best solution for your organisation? This is a difficult problem and understanding what solutions are good for today and fit for tomorrow is almost impossible without the sort of collaboration offered by the CCOE.”
David Woodfine
David Woodfine is the managing director of Cyber Security Associates (CSA), a company he started with former colleague James Griffiths in 2013. CSA began as a consultancy practice and still offers this trusted advisor service helping clients with aspects of cyber security such as assessments, help gaining certifications, incident response and general cyber road maps and development. CSA also provides 24/7 managed Security Operations Centre (SOC) services to help monitor, prevent, detect, investigate, and respond to cyber threats. Before starting CSA, Woodfine had a career spanning 28 years in the Royal Airforce, where he undertook a range of roles related to cyber security, including holding the position of Commanding Officer of the Ministry of Defence Cyber Defence Unit. “The CCOE is both an information sharing platform and a one-stop-shop offering a framework of services so local authorities won’t have to go to twenty vendors, they can just come to a safe pair of hands and know that if they buy something approved by the CCOE then it is world class. We can also share intelligence on threats and lessons learned which will be invaluable to public bodies. Being part of the CCOE may stop any future attacks through monitoring and sharing information and, if the worst does still happen, the CCOE can help with key aspects of recovery and help improve the ongoing cyber security posture.”
Dougie Grant
Dougie Grant is Managing Director Europe & Global Head Incident Management at Nihon Cyber Defence. He started his career in the military and from there moved to the private sector working in IT where he became interested in cyber security. From here, he progressed into law enforcement, spending eight years as the Cyber Lead for the Police Service of Northern Ireland where he started building online investigative capability looking at the online components of crimes. He finished his public sector career in the City of London Police seconded to GCHQ and NCSC where he spent five years as a Senior Coordinator at the National Cyber Security Centre (NCSC). He remains associated to the NCSC as part of its Industry 100 (i100) initiative and holds an MSc in Forensic Computing and Cyber Crime Investigation as well as other certifications. “Opportunistic attacks are one the biggest threats we face. Anyone from the comfort of their living room can scan internet connected systems and networks globally to see if they can get in find vulnerabilities and exploit them to gain access and disrupt them, sometimes with catastrophic impacts. We have got to ensure that everything being acquired or used by the public sector is secure at its core and that is not there yet. If you are going to procure equipment or deploy technology or systems it is essential to understand the risk and threat and impacts of attacks and breaches which is something the CCOE can assist with.”
Councils urged to consider OT risks
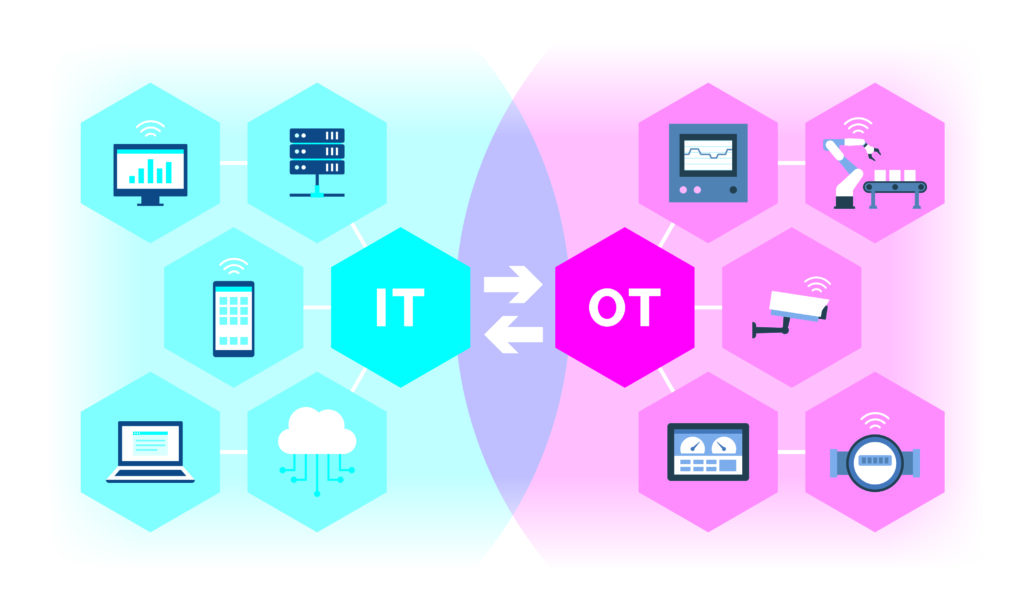
Local authorities are being urged to consider operational technology (OT) as part of their cyber security risk landscape, attacks on which could potentially result in serious health and safety incidents. Here is a brief list of just some OT a local authority may have which should be protected from direct or indirect cyber-attack:
- CCTV
- traffic light systems
- recycling plant processes
- lifts in real estate
- security-controlled doors
- fire control systems
- heating and lighting systems
- air conditioning systems
Operational Technology (OT) refers to technology used to monitor and control processes. Recent years have seen an increase in attacks on OT. The reasons are twofold: firstly, hackers have realised that OT often presents a vulnerable target and, secondly, systems are more integrated than ever before, increasing the likelihood that malware can move between IT systems and connected OT.
In May 2021, the Colonial Pipeline Company in America had to shut off its oil pipeline due to concerns that a ransomware attack on its billing system could spread to its OT network – an example of how an IT attack could compromise OT. While in July 2022, an Iranian steel manufacturer saw a hacktivist group target machinery causing a fire at its plant in an intentional direct attack on OT.
Local authorities might believe that they don’t have OT of any significance, but Major General Martin Smith CB MBE, the Managing Director of CyberPrism, a managed services company which protects Operational Technology (OT) and IT in the UK and internationally, said this is a commonly held misconception. OT that might be at risk of direct or indirect attack could include CCTV systems, traffic light systems, lifts, security-controlled doors, fire control systems, heating, lighting, air conditioning and more. In public services such as the NHS it can include equipment such as hospital scanners.
“There is a whole range of OT that local authorities won’t have addressed. The fact is that most organisations know nothing about their OT, so some form of basic assessment is a good place to start,” explained Major General Smith. “Until about two years ago those out there who wanted to hack into networks knew nothing about operational technology. They are starting to get the idea now as you can see from various attacks, such as the American Colonial pipeline attack. They now understand that attacking OT is good for two reasons. Firstly, it is vulnerable because organisations have not secured it. Secondly, if you can hack into OT, it is not just a case of stealing data, you can cause disruption. From a ransomware point of view, it becomes even more powerful. What if I stop the lift? Tamper with security-controlled doors? There is a considerable health and safety element too.”
Dane Clackworthy, Head of Business Development and Sales at CyberPrism, encouraged local authorities to take stock of their OT and look at how to protect it. “Every organisation knows that they need to secure their IT but not everyone knows about OT. There is a real gap in understanding what OT is and how we can protect it. One of the first steps is knowing what OT the organisation has. If you don’t know what you have, you can’t protect it and that is an inherent vulnerability.”
There is little doubt numbers of OT attacks are increasing. According to a report, OT Security Incidents: 2021 Trends and Analyses, the number of attacks with physical consequences in process and discrete manufacturing industries more than doubled in 2021 compared with 2020. The authors of the report predicted that ransomware-induced OT outages would triple in 2022 over 2021, stating that due to production outages and other physical consequences, attackers are realising that there is a likelihood ransoms would be paid. State[1]on-state attacks are also increasing. In 2022, for example, a sophisticated malware attack attempted to destroy the Ukrainian national grid as part of the Russian and Ukraine conflict.
One of the key strategies organisations can take is to segregate OT and IT and introduce software which will shut parts of the network off when a threat is detected without stopping the processes from taking place. “Networks are becoming ever more connected together which means that if malware gets into one area it could pass into everything. What you need is a more closed system where you know exactly where the gateway is, and you can segregate the systems effectively,” explained Major General Smith.
Also important are systems for monitoring activity and alerting to threats, while OT cyber security training is essential for staff and board members. One thing is clear, doing nothing is not a safe strategy. “While we might not yet quite be at the point where local authorities are being targeted through OT, attackers don’t have to attack the OT specifically to cause an effect. It could be an IT attack which could filter through to OT and have serious consequences. We know these types of attack will become more prevalent,” Clackworthy warned.
Both Major General Smith and Dane Clackworthy from CyberPrism are part of the Cyber Centre of Excellence (CCOE) Advisory Forum. The company provides consultancy services, such as OT audits, and access to specialised software-as-a-service to protect OT.
South Staffs Aims to be Most Protected Cyber Region

South Staffordshire District Council is moving further towards its goal of making its geographical area the most protected in the country from cyber-attack.
South Staffordshire implemented AppGuard in 2020 through iESE and its relationship with Assurity Systems, the European distributor of the product. Peter Shakespear, Corporate Director Finance & Resources at South Staffordshire Council, explained that the pilot would subsidise the implementation of AppGuard in one or two of its local parishes for a period. He said he was confident AppGuard would demonstrate its ability to prevent security breaches.
South Staffordshire Council is convinced by the technology having seen many other local authorities hit the headlines in recent years due to attacks which have caused high levels of damage to operations, resulting in high spend in recovery costs and untold reputational damage with customers. “Other local authorities have not had this protection and it has cost them millions of pounds,” said Shakespear, “For our parishes, this gives a solution that is integrated and matched with the district. After the trial we will hopefully have 27 parishes asking: Where do we sign?”
In addition to showing that AppGuard can prevent cyber-attacks, Shakespear said the trial should also demonstrate that the parishes taking part could potentially scale back some of their other protection, allowing some savings to be made.
As part of its objective to make South Staffordshire the geographical area most protected in the country from cyber-attack, the district council is also offering local businesses access to AppGuard at preferential rates through its business place partnership. “It is great to be able to go to a small parish council or a small business and tell them they can have a level of cyber security they never imagined and that we can make that accessible through iESE. Signing up is common sense. For me this isn’t a nice-to-have, this is the reality of the 21st Century. Cyber-attacks are increasing by the day, and we have to be one step ahead. Other solutions on the market are one step behind. It is an absolute essential,” he added.
Brad Collier, an iESE Associate who has been working with South Staffordshire on its implementation of AppGuard, praised the council for its foresight. “iESE set a mission five years ago to make the UK the safest place to live and work in Europe one local authority at a time. South Staffordshire are an innovative council making this a reality. The pilot is going to open the eyes of the parish councils as to how simple it is to protect themselves and their organisation. It is not complicated or expensive. New customers need to spend a short amount of time doing a survey and then installing the licence is a 20- minute process. In less than an hour it is possible to take away the pain that might occur from a targeted cyber-attack that could disrupt your whole business.”
What is AppGuard?
AppGuard is an endpoint cyber security solution which will protect your systems from all threats – even the never-seen-before attack known as ‘zero[1]day’. Developed in the US defence environment, it has recently become commercially available in the UK and is being offered to local authorities by iESE through a partnership with its European distributors, Assurity Systems Ltd.
AppGuard offers the required step-change in endpoint and server defence because it operates in an entirely different way to traditional solutions. The patented technology monitors everything and trusts nothing, meaning it offers full protection without the need to detect previously known exploits.
iESE has teamed up with Assurity Systems Ltd to bring this exciting, transformational technology to the UK’s local government environment. We have secured highly preferential rates (discounts exceeding 50 per cent) meaning you can benefit from this technology for around £45 per annum per endpoint for a fully-managed solution, including licence fees. A server version is also available and if you need extra monitoring and support, we have also secured preferential rates on Security Operation Centre (SOC) services.
Bringing AppGuard to Schools
Another organisation set to trial AppGuard is Gloverspice School, an independent special school situated on a care farm in the Midlands. Headteacher, Lynne Duffy, has become concerned about the risk of cyber[1]crime and the potential impact on students following an attack on a nearby local authority maintained secondary school.
Although her school isn’t large, the headteacher realises cyber-attacks are indiscriminate, highlighting that the school would not be able to afford to pay a ransom. Although the organisation has existing protection, she believes schools are vulnerable due to lack of expertise, time and budgets. “Taking part in a trial is a really good opportunity. I think cybercrime is quite frightening and that local authorities need to do more training with headteachers on cyber security. A lot of the information available is not specific for schools,” she said.
She would like local authorities which subscribe to AppGuard to offer their preferential rates to schools too, including special schools such as her own. “Hopefully local authorities signing up to AppGuard will allow schools in their area to buy into it as well, including those they use for specialist placements. My students’ fees are paid by the local authority so they should be supporting schools like ours as well as those which are local authority maintained,” she added.
CCOE Provides Access to NCSC-Accredited Training
Local authorities are being urged to consider operational technology (OT) as part of their cyber security risk landscape, attacks on which could potentially result in serious health and safety incidents.
The Cyber Centre of Excellence (CCOE) has teamed up with UK Government-certified cyber security and awareness training provider OSP Cyber Academy to provide access to a wide range of cyber security and data protection training programmes.
Through the CCOE, local authorities and other public sector bodies can access OSP Cyber Academy’s Cyber/Information Security and Data Protection training, which is National Cyber Security Centre (NCSC) certified. Training days, such as the Cyber Risk & Resilience Board & Executive Awareness Course, will be offered in person for executives, while an online system will also be available to allow an organisation’s wider employee population to access various online courses. These will include: OSP’s GDPR Staff Awareness Course, Cyber Security Staff Awareness Course, Phishing and Social Engineering Course and Mobile Device Security Course and the newly developed Supply Chain Cyber Awareness Course.
These courses will help reduce risk, improve cyber resilience and demonstrate compliance with legal requirements. Thomas McCarthy, Managing Director at OSP Cyber Academy, said training and awareness must start at the top of the organisation but that it was also vital this filtered down to the wider employee population for maximum benefit.
One reason is that cyber risk is greatly increased by employee error, such as unwittingly clicking on an unsecure link. Irene Coyle, Chief Operating Officer at OSP Cyber Academy who is one of the company’s training leaders, said education and awareness were important and that this must be continuous due to the rapid and ever-changing nature of cyber threat. “Public authorities are a real target. Cyber attackers are looking to be disruptive and to cause chaos. Having strong policies and training in place can greatly reduce risk exposure.”
However, she said it was vital cyber security and data protection were not viewed as ‘box-ticking’ exercises. Even where senior management can demonstrate compliance, such as by having a data protection policy in place, Coyle highlights that this is not enough – staff have to be aware of such policies and why they are important too. “When you can show the relevant policies are in place, that is great and it has ticked the box, but is that policy known by the users of company devices, do they follow it and how do you know that they follow it?,” she asks. “The key thing is education and awareness and that must be continuous. You can have any certification you want but that doesn’t mean you are reducing the vulnerabilities your people may create.”
McCarthy said OSP Cyber Academy was providing training at the highest standard: “We are a NCSC-certified training provider, which is not something any organisation can say. We are the leaders in what we do in cyber protection training and data protection training. We also know the other organisations involved in the CCOE are all equally credible which is what makes it so exciting to be a part of.”
To find out more about OSP Cyber Academy visit: www.ospcyberacademy.com
To book cyber training at discounted rates for local public services, please go to: www.ccoe.org.uk
Increase Diversity to Fight Cyber Crime
Local authorities are being encouraged to look at the diversity of their workforce to help tackle cyber-crime against their organisations.
While there is a moral case for diversity and equality in the workplace, a more diverse and inclusive workforce can also help strengthen your cyber security defences, experts believe.
Sandip Patel KC is a Barrister who is part of the CCOE Advisory Forum. He hopes the CCOE can help local authorities diversify their teams with cyber responsibilities to help give broader insight into cyber-crime in their organisations: “When you go along to cyber conferences the attendees and speakers are 98 per cent male and white and the industry is heavily dominated by ex-military and ex-M15 personnel and law enforcement. There are 7000,000 vacancies in the United States alone in cybersecurity – they can’t all be filled with men with a certain background,” he said.
Patel is optimistic things are starting to change, noting greater evidence women of in key roles. He also believes neurodiversity within cyber teams is important when thinking about the adversary you are facing. “In my experience of prosecuting, those conducting cyber-crime tended to be young men, but they don’t fall into the classical category of a criminal. These are often sophisticated individuals who are often brighter than you – often on a genius level,” he noted.
Irene Coyle, Chief Operating Officer at OSP Cyber Academy, is also on the CCOE Advisory Forum. When working in police recruitment she launched the Positive Action for Women programme which aimed to uncover barriers for women. The programme was successful in increasing numbers of female employees, later becoming a programme for all minority groups. Coyle now advocates for diversity in cyber through giving talks and actively challenging companies to tackle the issue.
Coyle believes increasing the talent pool of young people through apprenticeship schemes and work placements is something local authorities should consider. “This might sound ageist, but young people can be more attuned to the cyber landscape. Having a much more diverse workforce in cyber security will allow you to learn from them and try to build your defences better. You don’t know who is behind the mask because cyber- crime is a faceless crime but having a more diverse workforce will help meet the challenges you face.”
A recent report by the National Cyber Security Centre (NCSC) and KPMG, Decrypting Diversity: Diversity and Inclusion in Cyber Security, painted a mixed picture of the cyber security industry. An area where the report calls for further diversity is age, with only one in twenty respondents’ categorising themselves at between 18 and 24 years old. Jonathan Gill, a Partner at KPMG, said the UK needs a thriving cyber security sector to remain safe and prosperous. “Diversity and inclusion are fundamental to this because we need to attract and retain the best talent and foster diversity of thought,” he said.
To find out more about the CCOE, please go to www.ccoe.org.uk or contact us directly at [email protected]




