The year of 2022 was remarkable in terms of significant rise in the number of Distributed Denial of Service (DDoS) attacks and their intensity worldwide. The duration of DDoS attacks rose tenfold in 2022 compared to 2021, demonstrating increasing capabilities from the attackers in terms of their hardware.
Number of IP Addresses Involved in Malicious Activity in 2022
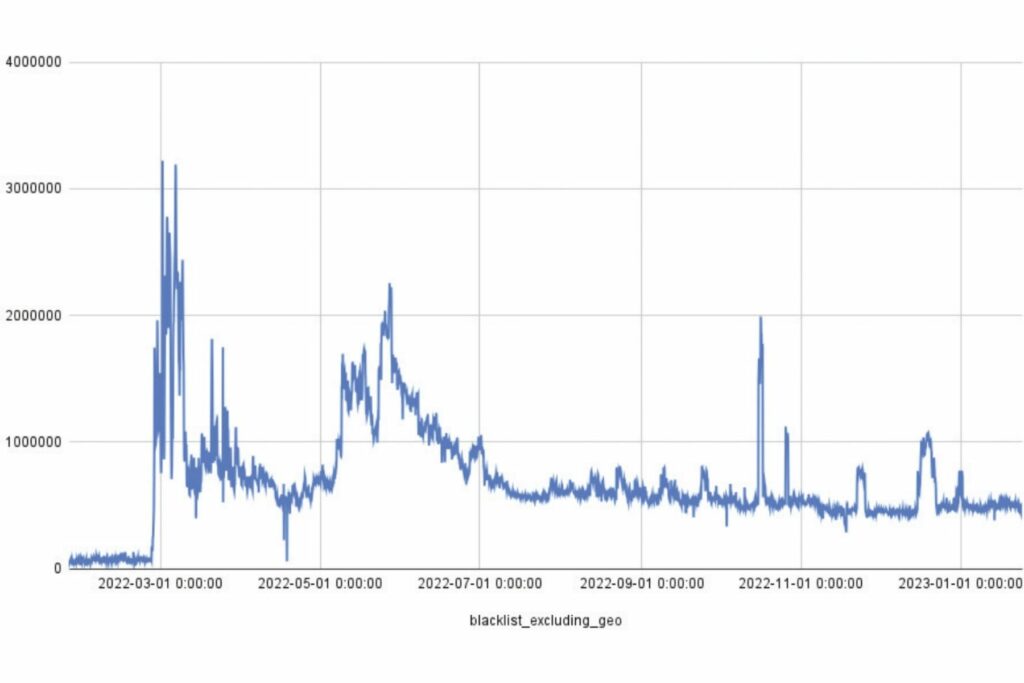
According to our recent survey, the total number of attacks in 2022 increased by 73.09% year-on-year. Cybercriminals mainly focused on media (18.5%), banks (9.9%), and payment systems (13%) with the latter two being the most profitable sectors, in terms of arranging cyberattacks.
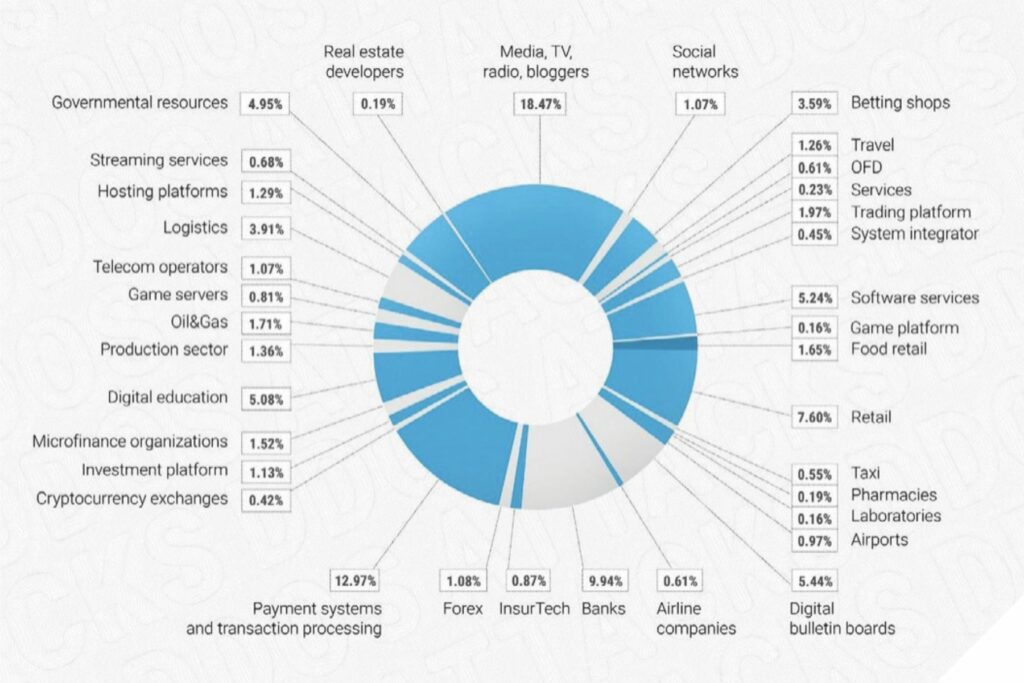
Number of DDoS Attacks by Industry in 2022
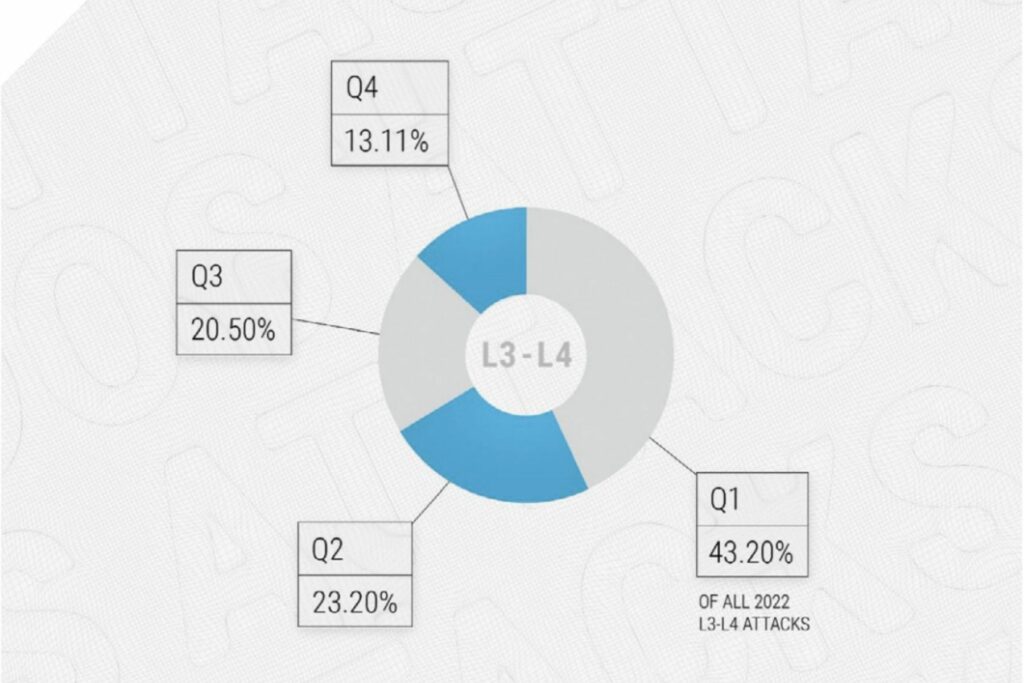
The largest share of attacks occurred in the first quarter of 2022 which was 43.2%, and it then began to decline in the second and third quarters to 23.3% and 20.5%, respectively. The fourth quarter observed just 13.11% of the annual number of attacks.
Quarterly Distribution of DDoS Attacks in 2022
The duration of DDoS attacks increased tenfold YoY. While in the first quarter of 2021, the maximum duration was 10 hours, in the same period of 2022, it was 10.5 days. In addition to the rise in intensity, starting from the fourth quarter of 2022, there was an increase in the complexity of attacks.
At the beginning of 2022, most attacks were simple. It wasn’t until Q4 that we began to see a surge in their complexity. At a certain point, basic attacks were no longer effective: the industry had learned how to deal with them, and cybercriminals started to escalate the difficulty in order to get results.
While attackers previously sought to optimize botnet usage time, they now have the resources to continue their attacks for weeks. The quantitative peak is over – unpretentious mass cyberattacks, which many web resources quickly and successfully «knocked down», have worked their way through.
Now, we expect a new stage in the competition between the armor and the projectile. Instead of mass, the attackers are tasked with achieving efficiency. The sophistication of attacks will grow, and methods of neutralizing them, which were effective yesterday, will most likely not work tomorrow.
This pattern will become common for any services, both public companies and private businesses.
It’s actually hard to say if the infrastructure will be able to cope with such attacks, since this will be influenced by a large number of factors, one of which is the amount of investment in infrastructure. If the infrastructure development stops, it may cause huge risks in terms of its ability to successfully mitigate large amount of sophisticated attacks.
In 2023, we expect Application Layer DDoS attacks, with their traffic mimicking the behavior of ordinary users, to become more widespread. Such attacks are extremely challenging to detect and neutralize.
In terms of the Internet threats, the top three will not dramatically change this year. DDoS attacks, phishing and hacking take up positions in the ranking of the most common threats on the Internet year by year, just exchanging their positions once in a while. Therefore, in 2023, we don’t expect emergence of fundamentally new types of threats.
The Way for Companies to Tackle the Challenges in 2023 Head-On
In conclusion, two important tips for market participants on the ways to protect themselves and their customers from cyber fraudsters in 2023.
Foremost, a company has to know the network and its services well. Services should be split into different baskets depending on their risk and severity level to the business (mission critical, critical, bulk, etc.). For each of these baskets, a risk assessment should be performed, and these risks should be managed (risk mitigation).
It is also important to deploy cyber defenses on a permanent basis (“always-on”). If there is no such a solution, it is required to conduct internal drills switching to incident-service in response to test attacks at least quarterly. In addition, network services should be reanalyzed at least twice a year: what the network consists of, what applications are in it, which of them are critical, and what are the risks for them. Such an approach will help to counter cybercrimes effectively and help the company services to stay up and running 24/7 increasing customers’ loyalty and maintaining a good business reputation as a reliable and honest service provider.




