Article by Mohamad Mahjoub, CISO – Veolia Near and Middle East
It is no secret that Cyber Attacks are on the rise. The utilities market has been experiencing such kinds of attacks since 2015. Our Group’s size, international scope and the variety of its businesses make it all the more vulnerable to cyber risks and prone to be the target of cyber attacks. Moreover, as a world leader in utilities management, Veolia wishes to be ahead of regulations which are more and more enforced. Cyber threats are becoming more sophisticated and prevalent as we continue to rely on digital technologies to drive business growth. In today’s digital age, the role of the Chief Information Security Officer (CISO) is more important than ever to secure the digital future of any organization.
As a CISO, my primary responsibility is to implement and oversee Veolia Near and Middle East cybersecurity program. This includes identifying potential cyber risks and ensuring that Veolia Near and Middle East is prepared to handle any cyber incidents that may occur. It is vital as well to align the cybersecurity program with the overall business objectives and strategy. By understanding the company’s goals and objectives, I can ensure that the cybersecurity program is in line with them. By aligning cybersecurity and business objectives, CISOs can help the company achieve its goals and protect its digital assets.
Monitoring incident response activities is another critical responsibility. Cyber incidents can occur at any time, and we need to be prepared to respond promptly and effectively. By monitoring incident response activities, we can ensure that Veolia Near and Middle East is ready to handle any potential cyber incidents and minimize their impact on the company’s operations.
Managing business continuity and disaster recovery is one of the most important areas for a CISO to manage. A cyber incident can cause significant disruptions to our company’s operations, making it essential to have a plan in place to ensure that the company can continue to operate in the event of a disaster. I am responsible for developing and implementing a business continuity and disaster recovery plan that will enable us to recover from any cyber incidents quickly.
Cultivating a strong information security culture is another key responsibility. I have created an environment in which employees understand the importance of cybersecurity and its role in protecting the company’s digital assets. This is a pre-requisite to pave the way to a cyber security awareness and training program, which is an essential task for any CISO. I try my best to ensure that all employees are trained on cybersecurity best practices and understand the potential risks associated with cyber threats. Topics include social engineering, how to identify phishing scams, how to avoid BEC attacks, and many more.
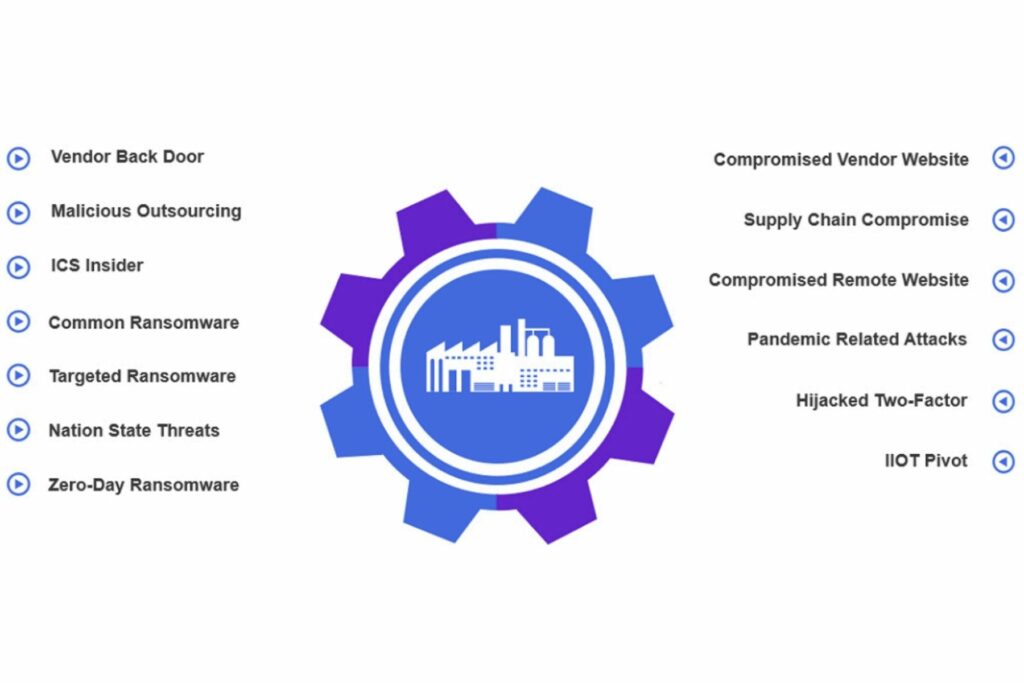
Everyone is fighting against a remarkable IT and OT threat landscape; Veolia Near and Middle East region is no different. As you may be aware, some threats identified in the diagram have the potential to evolve into disruptive and destructive capabilities, particularly the supply chain and ransomware attacks. On top of that, ransomware gangs are an emerging constant threat due to the fact that they share methods, infrastructure (C&C), and techniques.
Ransomware-as-a-Service (RaaS) has also emerged to be a common term where malicious ransomware packages are made available to other criminals, who can easily make use of them. Moreover, the majority of the industrial environment is vulnerable to newly known defects (ripple 20 and amnesia), misconfigurations, and inadequate maintenance, which is in turn assisting these threats to materialise. The main challenge is that we always need to be vigilant about new threat vectors for IT and OT environments.
We all know that risk can be reduced by implementing a well-maintained defence-in-depth approach, which is exactly what we are continuously working on. We believe that the governance umbrella, in addition to employee cyber awareness and having a defined and tested incident response procedure in place, is the cornerstone of this strategy. We are currently deploying OT vulnerability management solutions across the region, which will provide us with many security benefits. We believe that such initiatives go hand in hand with the need for digital transformation and corporate modernization. We are constantly working with our peers all over the world on securing our systems to meet these demands and, as a result, business needs, while taking into account the uniqueness of local and relevant cyber legislations.
OT security has always been a challenge to us, that being said, we are benchmarking global standards such as NIST CSF, NIST 800- 53, NIST 800-82, and ISO 27001:2022 and the seamless integration of GDPR in it, and ISA/IEC 62443 to building our internal “Security Framework” to help us provide a consistent language for the security community across Veolia, this will in turn assist us to analyse and effectively convey our security posture, away from the intricacies of frameworks and standards.
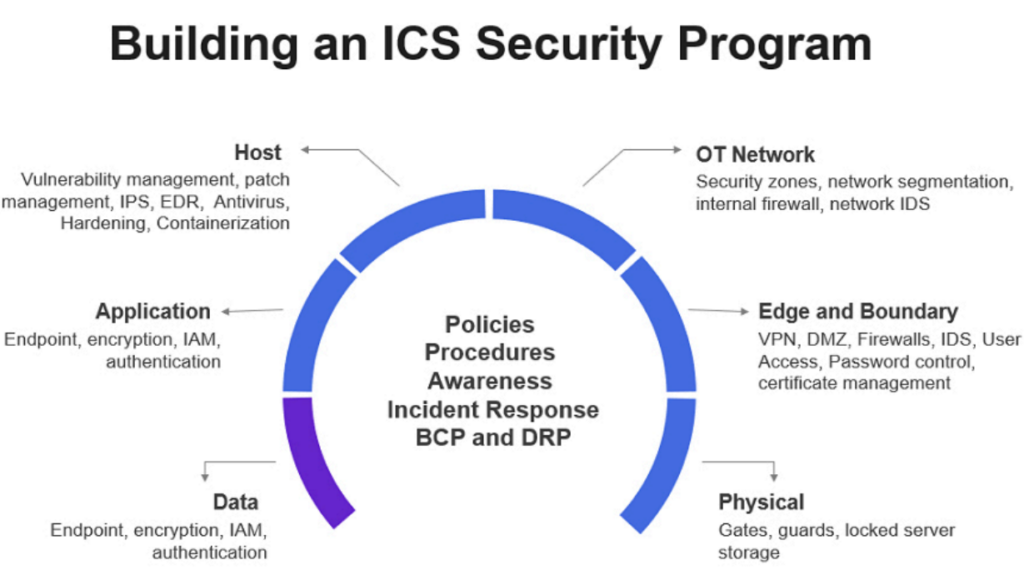
The rule of thumb is “Threats can be mitigated through a well-maintained defense in-depth strategy”. Industrial environments are no different. Data, application, host, OT network, edge and boundary, in addition to physical security layers must be carefully assessed before relevant security controls can be implemented. The most important factor is the governance aspect and management support, employee’s awareness, existence of solid policies procedures, in addition to having resilient incident response and business continuity plans.
My advice to corporate cyber security teams is to go to their plants, understand the process well, learn the language of the OT people, and build relationship with them as this will help tackling cyber security concerns more efficiently.