Article by Dr Gareth Owenson, Co-Founder and CTO of Searchlight Cyber
The “dark web” has more than earnt the negative connotation that comes with its name. While there are some specific positive uses for this anonymised area of the internet, we know from our own research that the vast majority of activity on the dark web is explicitly illegal. This includes its use by cybercriminal gangs who target energy companies and other organisations from hacking forums where they believe they can act anonymously.
While this sounds scary, cybersecurity professionals are increasingly realising that the dark web offers them an opportunity. By monitoring the dark web, they can gain a better understanding of their adversaries, inform their defences, and even potentially spot attacks against them before they are launched. Indeed, our recent survey of CISOs found that 72 percent of oil and gas companies are gathering data from the dark web for defensive purposes.
However, while this is a promising start, there is still a long way to go. The energy industry uses dark web data less than comparable high risk industries such as financial services (85 percent), manufacturing (83 percent), and transportation (81 percent). Even more concerningly, more than a quarter (27 percent) of oil and gas CISOs still believe that activity on the dark web has no impact on their company at all.
This article will break that misconception by explaining what the dark web is, how energy organisations are targeted on it, and what they can do about it.
What is the dark web?
The dark web is distinct from the wider internet in that its sites are not indexed on standard search engines (like Google or Bing) and can’t be accessed via standard web browsers (like Chrome or Safari). It can only be accessed through specialist software such as The Onion Router (Tor), which has been designed to protect users’ anonymity when they search the web or host websites.
This perception of anonymity has made the dark web popular with cybercriminals who believe they can act with impunity, out of reach of law enforcement or cybersecurity professionals. However, while it is true that using the dark web does make the individuals harder to identify, their actions are far from invisible. In fact, cybersecurity professionals are increasingly monitoring the dark web to gather intelligence on threat actors operating on dark web forums and marketplaces, where they are effectively planning their attacks. This type of threat intelligence is known as “pre-attack intelligence”, as it refers to the activity of cybercriminals before a cyberattack is launched.
Pre-attack intelligence is incredibly valuable to a cybersecurity team because it gives them a chance to take preemptive defensive actions before their network is breached, providing a rare opportunity to completely prevent a cyberattack.
How are energy companies targeted on the dark web?
Our recent research found that the energy companies are primarily targeted in dark web forum “auctions”, where cybercriminals sell initial access to energy companies’ networks to other cybercriminals for them to exploit.2 The image below is a real example of a typical post that we have labelled to show the key components:
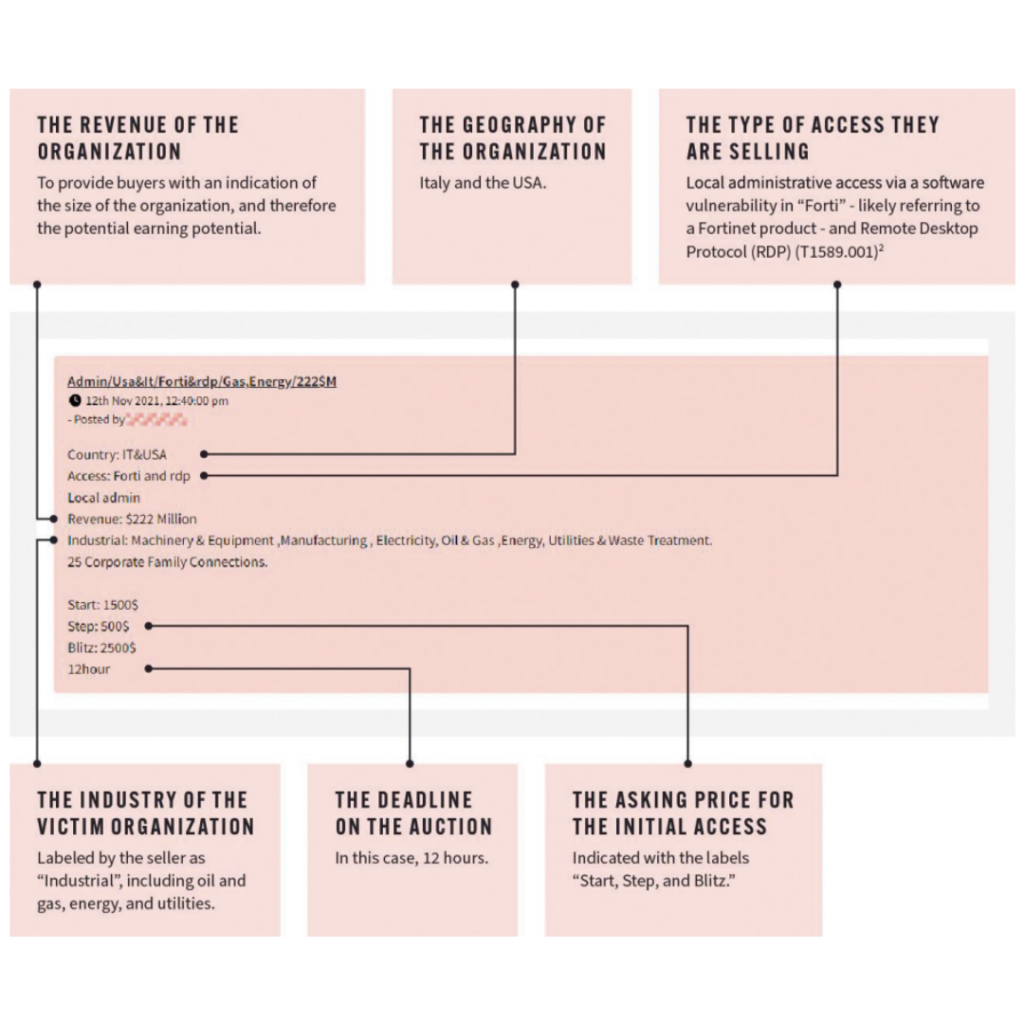
The “Start, Step, Blitz” terminology used in this post is a common approach to auctioning initial access on dark web forums. In this case, it means that bidding starts at $1500 and bids will be placed at increments of $500. However, if an individual wanted to purchase the access outright they could do so at the “blitz” price of $2500.
Initial Access Broker posts like these are a good example of pre-attack intelligence because, while this information is shared with the intention of attracting buyers, it also offers cybersecurity professionals a valuable opportunity to determine if their organisation has been compromised and is the subject of this dark web ad.
For example, with the information the seller provides on the revenue, location, and technology of the organisation, a security team could identify if they fit the profile of the victim. In some cases the company name is even given, which means that if the security team is monitoring the dark web they would be able to immediately identify that they are being targeted and take mitigative action.
The seller also names the technology that has been compromised (a Fortinet Remote Desktop Protocol), which would give the security team a starting point for their internal investigation. Other types of access we commonly observe being sold include Virtual Private Networks (VPNs) and stolen corporate credentials.
Threats to ICS and OT
While it is less common, our research also uncovered cybercriminals discussing ICS and OT systems on dark web forums and sharing files and resources to help others conduct attacks.
Compromised critical infrastructure is undoubtedly the highest priority concern of cybersecurity professionals at energy organisations and many will be concerned to hear that this technology is openly discussed on the dark web. However, once again, this simply highlights the need for security professionals to continuously monitor for evidence that their infrastructure is being targeted.
With intelligence on what systems are being discussed, what information the cybercriminals have, and what vulnerabilities they might be looking to exploit – security professionals can make far more informed decisions on applying additional security controls and monitoring their ICS for suspicious activity.
The case for dark web monitoring
The unfortunate reality is that energy organisations are increasingly in the crosshairs of cybercriminals. While they may not have historically been considered the primary target for financially-motivated cyberattacks, the threat landscape has changed dramatically over the past few years, and cybercriminals are no longer just focusing on asset-rich organisations like banks and insurance companies. They are increasingly targeting the energy industry to leverage the critical nature of these companies and extort ransoms.
This makes dark web intelligence vital. By monitoring the dark web, energy organisations can identify threats against their company earlier, use the intelligence they gather to inform their defensive strategies, and be much more proactive in stopping cyberattacks.




